Here are 5 analytical security questions to develop understanding of how various systems in Information and Network Security world work; the broad security areas covered are HTTP Strict Transport Security (HSTS), SSL and deployment, Wireshark and Packet sniffing, Web Server Vulnerabilities, WEP Cracking.
HTTP Strict Transport Security (HSTS)
HTTP Strict Transport Security (HSTS, RFC 6797) is a header which allows a website to specify and enforce security policy in client web browsers. This policy enforcement protects secure websites from downgrade attacks, SSL stripping, and cookie hijacking. It allows a web server to declare a policy that browsers will only connect using secure HTTPS connections, and ensures end users do not “click through” critical security warnings. HSTS is an important security mechanism for high security websites. HSTS headers are only respected when served over HTTPS connections, not HTTP.
HSTS generally has the following behavior in user web browsers:
- Insecure HTTP links become secure HTTPS links
- SSL certificate warnings or other errors show an error message and cannot be bypassed by the user
Take a working (actual) website (Nepal based) and design (in connected series diagram or data flow diagram or mind map or any brainstorming representation) HSTS implementation for it. Think about server-client side, SSL, End-user, browsers and anything you think should be considered.
Apart from pictorial representation, the answer how the system works (bullet wise.)
SSL and deployment (based on CloudFlare cloud-based CDN & DNS service)
Use SSL in order to encrypt data, like credit card numbers, and other sensitive information while in transit to and from your website. SSL encryption ensures that communication between your visitor and website is confidential.
Additional benefits of SSL:
- Visitors have a way to verify that they are on your website and not that of an impostor
- Visitors can verify that your website’s content has not been modified in transit
- Your website’s search engine ranking may be improved
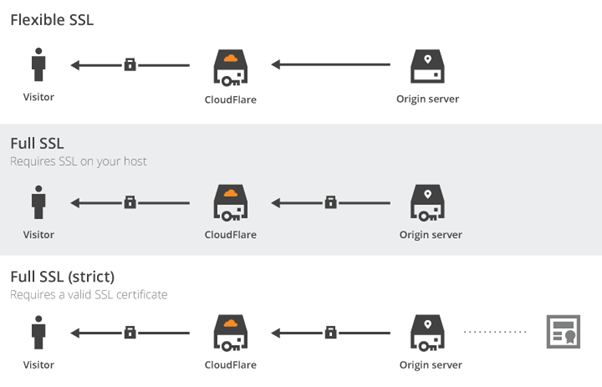
What SSL setting should I use?
- Flexible SSL:There is an encrypted connection between your website visitors and CloudFlare, but not from CloudFlare to your server.
- You do not need an SSL certificate on your server
- Visitors will see the SSL lock icon in their browser
Full SSL: Encrypts the connection between your website visitors and CloudFlare, and from CloudFlare to your server. The difference between Full and Full (Strict) is that Full (Strict) checks for a valid certificate on your origin server, whereas Full checks for any certificate.
- You will need to have an SSL certificate on your server. However, CloudFlare will not attempt to validate the certificate (certificates may be self-signed)
- Visitors will see the SSL lock icon in their browser
- Full SSL (strict):Encrypts the connection between your website visitors and CloudFlare, and from CloudFlare to your server.
- You will need to have a valid SSL certificate installed on your server, and the certificate must be signed by a trusted certificate authority and have not expired
- Visitors will see the SSL lock icon in their browser
- Strict (SSL-Only Origin Pull): The mode will upgrade all connections between CloudFlare and the origin from HTTP to HTTPS, even if the original content requested is over HTTP. This mode will only accept valid certificates on the origin server. That means that you will need to have a valid SSL certificate installed on your server, and the certificate must be signed by a trusted certificate authority and have not expired.
Figure Sample Certificate Deployment
Take Nepal based websites or web portals to consider each of the 4 possible ways of SSL deployment on them. You can assume CloudFlare has a service directly running from Nepal or name any similar service.
Prepare a tabular representation of these possible SSL deployment plan with the 4-different websites you opted for on each of the plan. Mention why these websites fit the SSL Plan you just opted for.
Draw (in connected series diagram or data flow diagram or mind map or any brainstorming representation) any one of the SSL Plan for the website you mentioned.
Wireshark and Packet sniffing
What you can do with Wireshark?
What Wireshark does is sniff out the packets being passed around your network—whether they’re heading to or from your computer or to or from other computers on the same network as you—and let you poke around at the data passed back and forth in these packets.
When you log into a web site, for example, your browser sends what’s called a POST request to a server somewhere on there on the internet. Wireshark can capture that POST request, and if you know where to look, you can find your username and password in plain text—assuming you’re logging into a site that isn’t using a secured HTTPS connection, which will encrypt that information so you wouldn’t be able to make sense of it.
Official PCAP Next Generation Dump File Format & PCAP-DumpFileFormat documentation is available at https://www.winpcap.org/ntar/draft/PCAP-DumpFileFormat.html
Now, create your own network (hotspot) and using it in your group. Develop a simple login authentication form and run it (either on localhost or on network.) Using Wireshark trace actions incurred during your login form deployment (and sign in or submit CTA). Take a screenshot of major events and mention what’s happening. Highlight the rows that contain CTA information. And propose your own solution to prevent such sniffing.
Draw (in connected series diagram or data flow diagram or mind map or any brainstorming representation) to represent how packet was captured and sniffing was done in the entire process.
Web Server Vulnerabilities
The common weakness or vulnerabilities that the web server can take an advantage of are
- Default settings
- Misconfiguration
- Bugs in operating system and web servers
Below are the techniques used to prevent web server attacks.
- Patch Management
- Secure installation and configuration of the O.S
- Safe installation and configuration of the web server software
- Scanning system vulnerability
- Anti-virus and firewalls
- Remote administration disabling
- Removing of unused and default account
- Changing of default ports and settings to customs port and settings
Figure Sample server and connectivity
Your web server also hosts email exchange server feature and ADDS. Device all possible security measures including security certificates to your server.
Draw (in connected series diagram or data flow diagram or mind map or any brainstorming representation) to represent how your security measures have been deployed. Also include a bullet wise explanation of each steps.
WEP cracking
WEP cracking is the method of exploiting security vulnerabilities in wireless networks and gaining unauthorized access. There are basically two types of cracks
- Active cracking: Until the WEP security has been cracked this type of cracking has no effect on the network traffic.
- Passive cracking: It is easy to detect compared to passive cracking. This type of attack has increased load effect on the network traffic.
Various tools used for WEP cracking are
- Aircrack
- WEPCrack
- Kismet
- WebDecrypt
Create your own ad-hoc network with WEP as security or use a WEP supported home router. And try to crack your WEP security. Mention in bullets how did you crack the security.
Draw (in connected series diagram or data flow diagram or mind map or any brainstorming representation) to represent how the entire process of cracking WEP went.